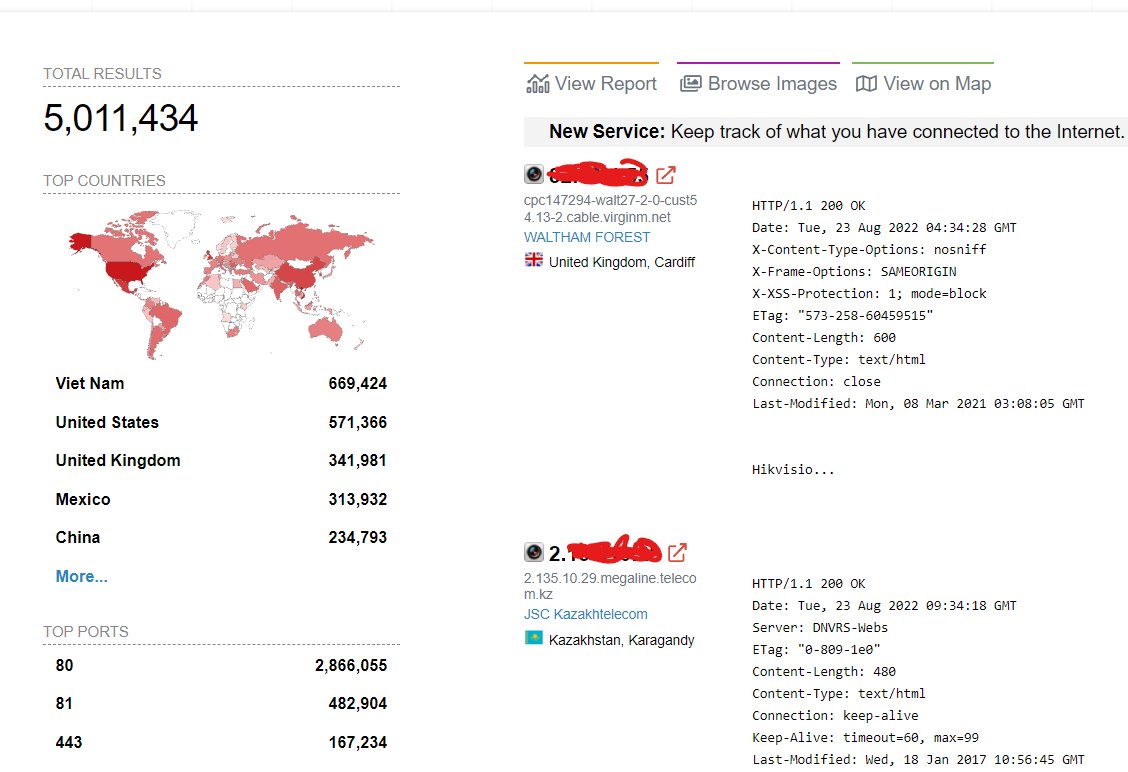
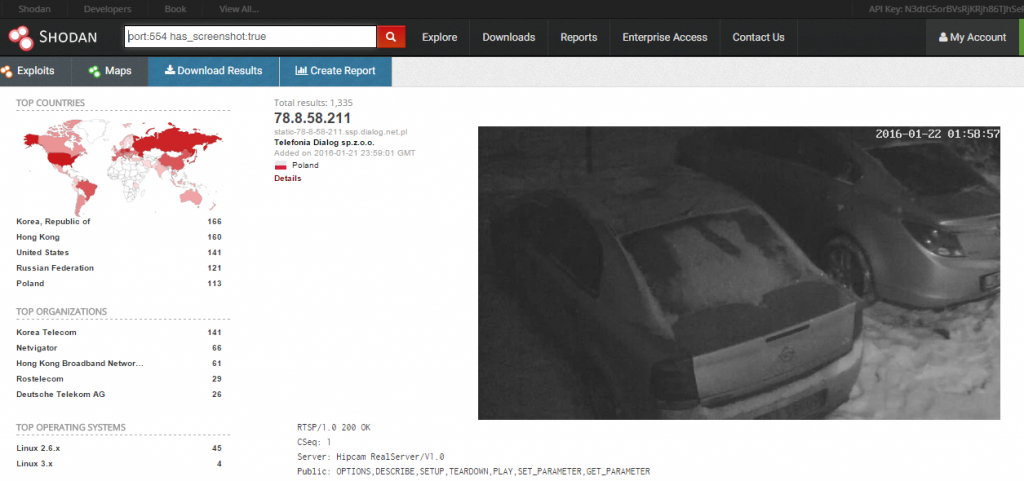
Sunny Nehra on Twitter: "2/ Almost on all private as well as public forums, you can find threat actors selling lists of the vulnerable Hikvision CCTV Cameras. On Shodan there are over

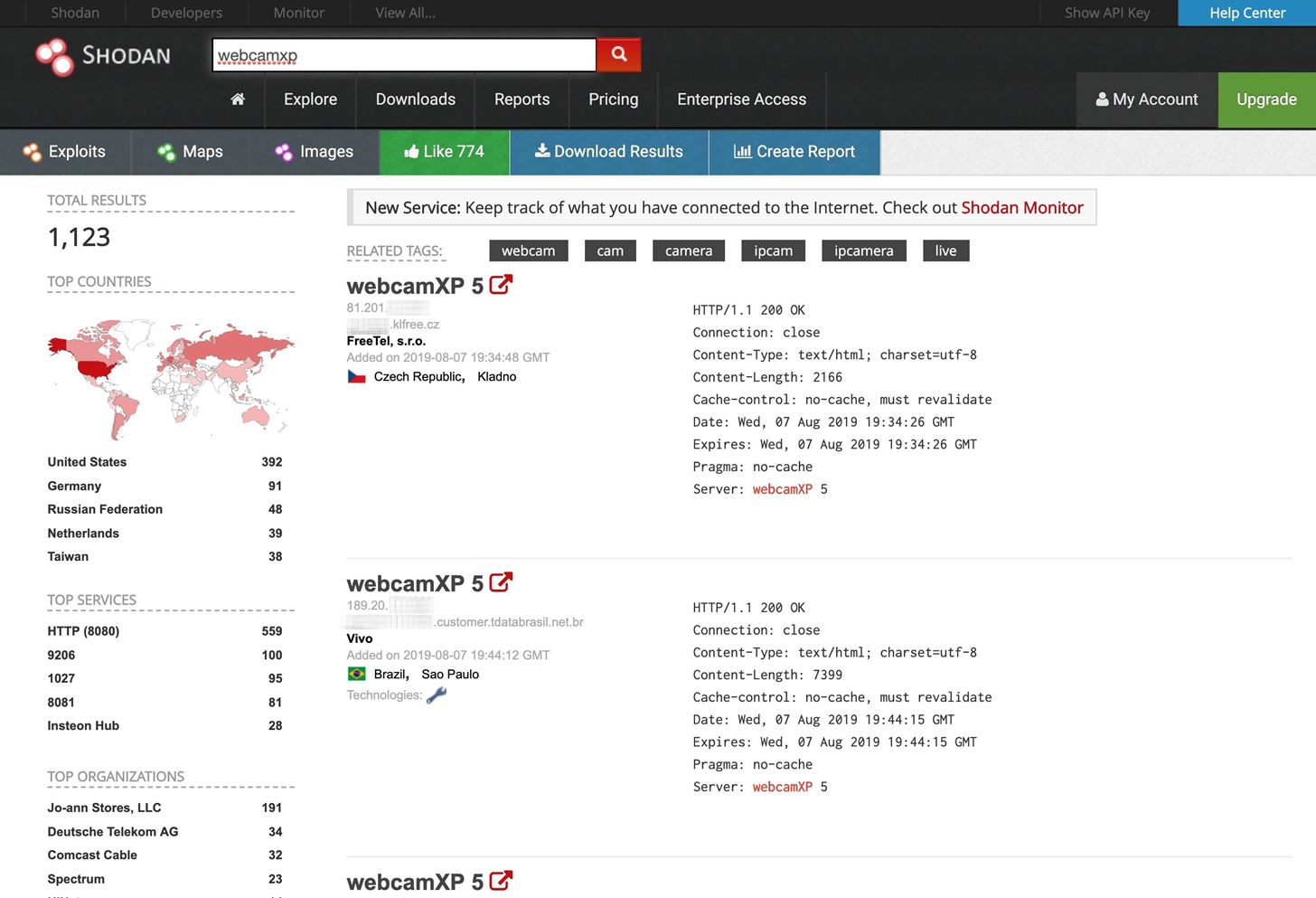
PenTest Edition: Using Shodan to Locate Internet-Connected Devices (Webcams, Servers, Routers, and More) – The Cybersecurity Man

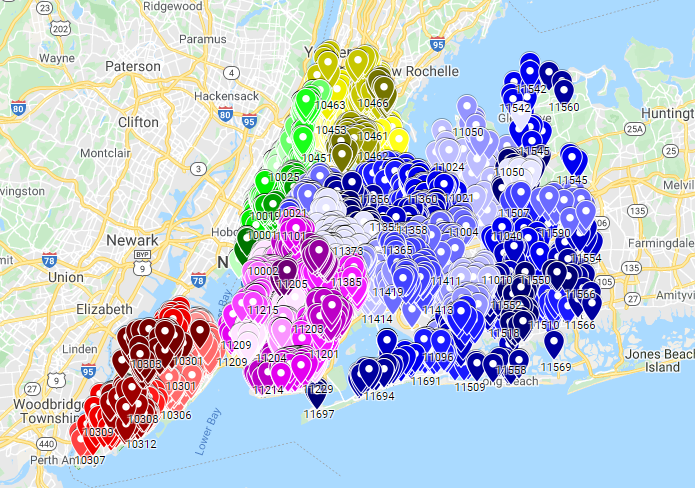
A list of home surveillance cameras device–scanning search engine Shodan | Download Scientific Diagram


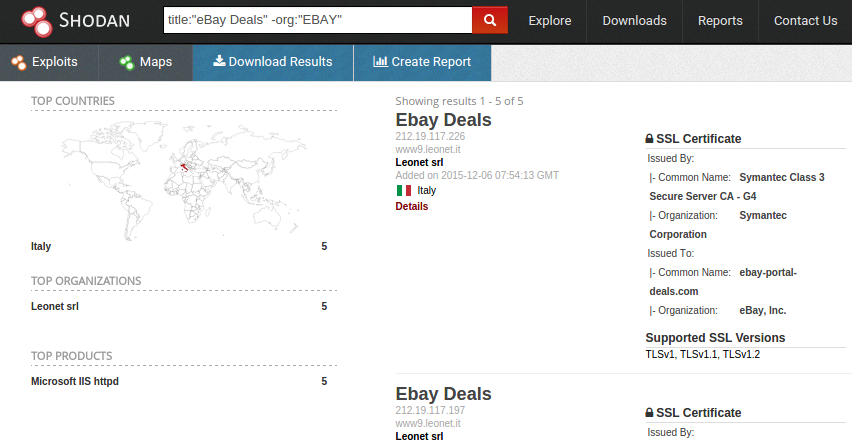
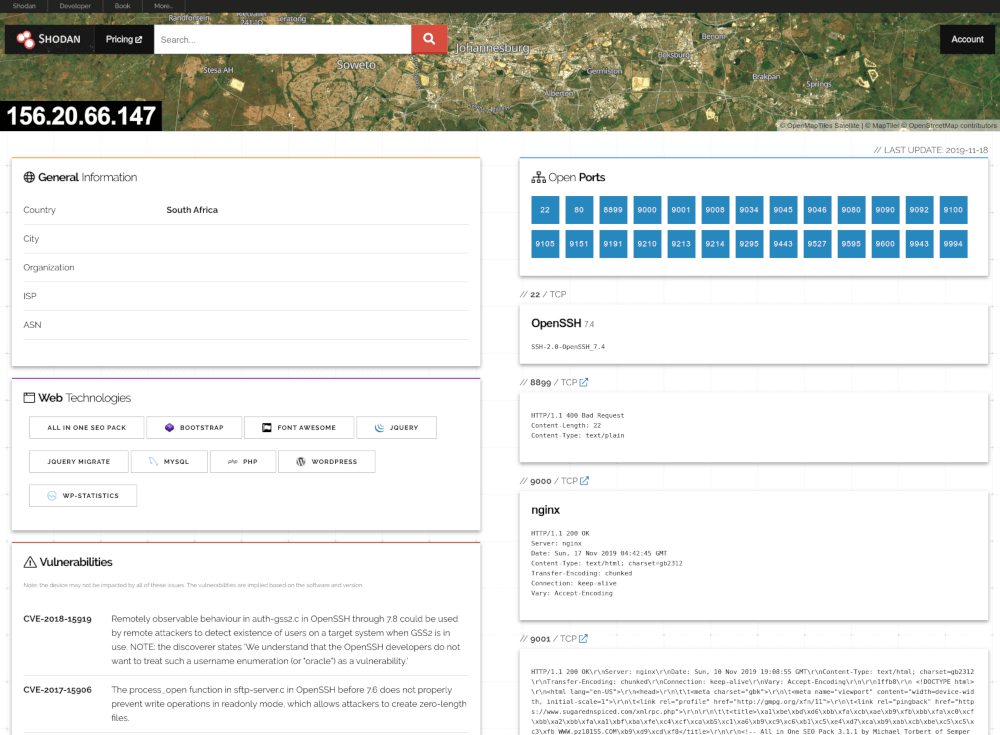

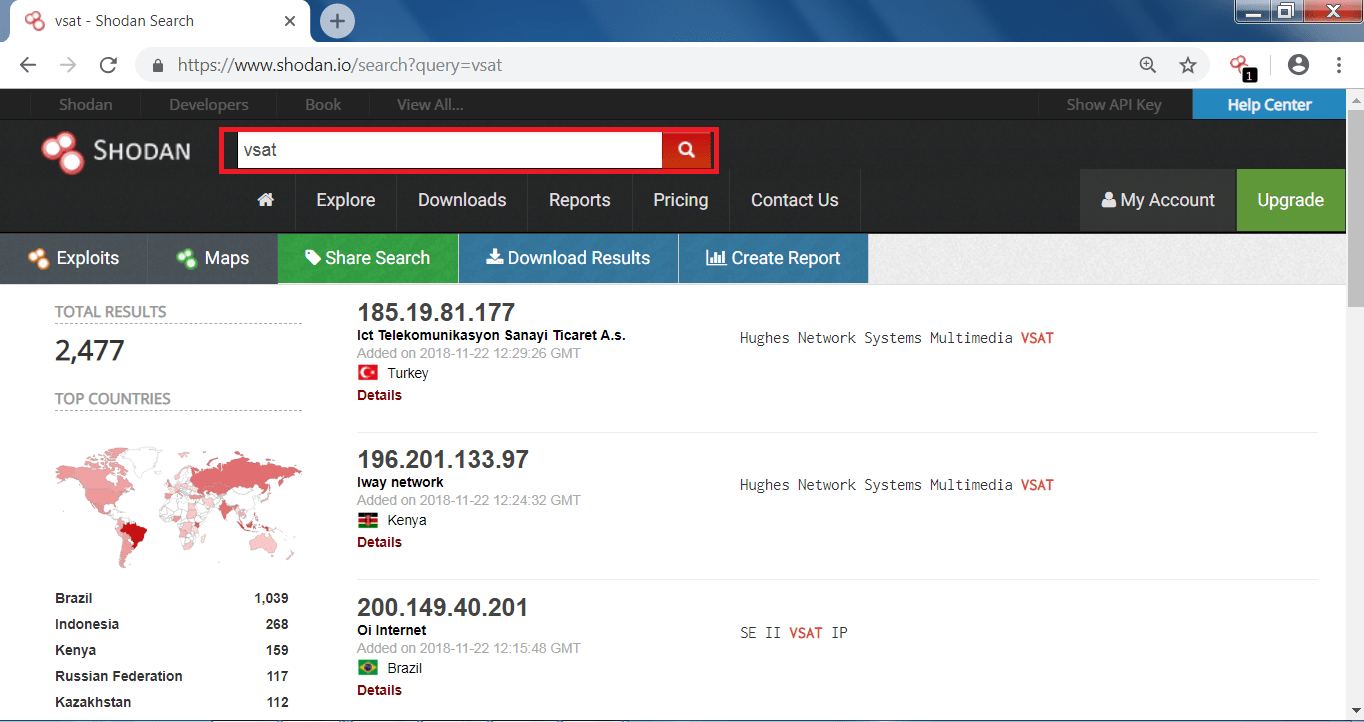


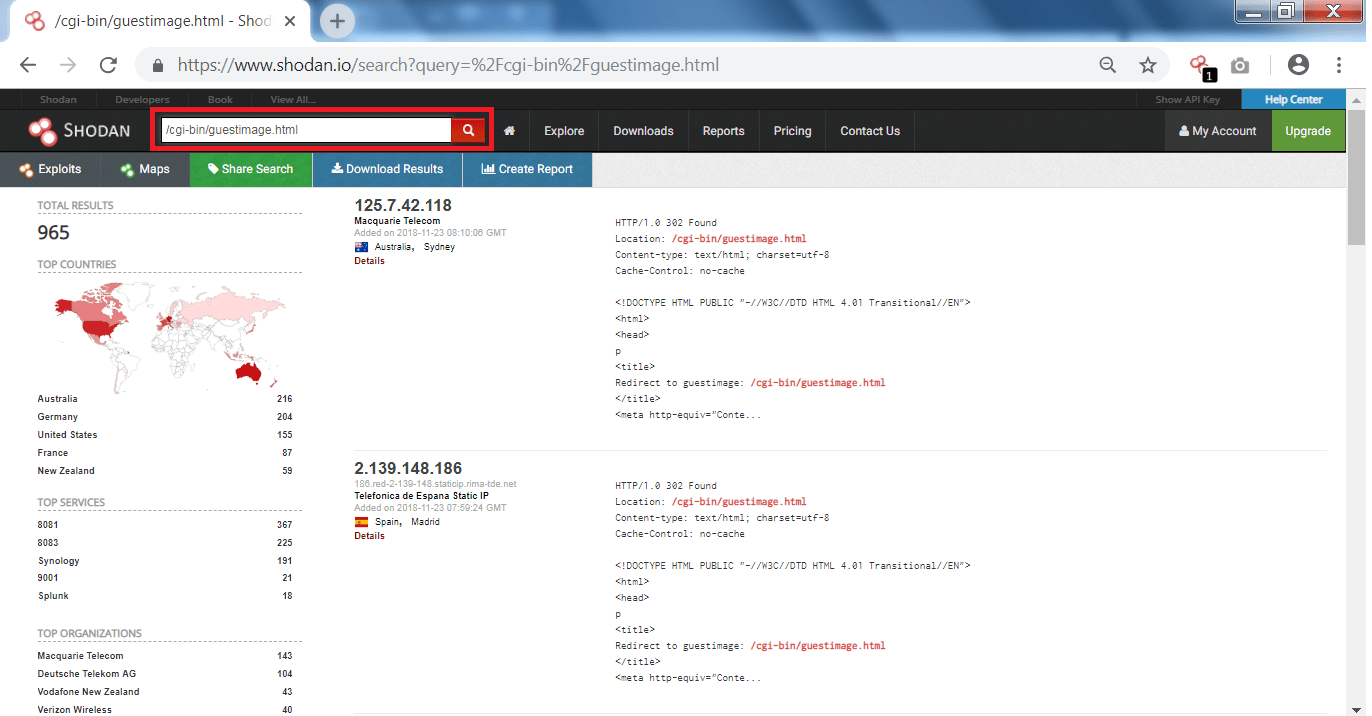
![Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube](https://i.ytimg.com/vi/oDkg1zz6xlw/maxresdefault.jpg)
![Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube](https://i.ytimg.com/vi/i7PIyCq_VU4/hq720.jpg?sqp=-oaymwEhCK4FEIIDSFryq4qpAxMIARUAAAAAGAElAADIQj0AgKJD&rs=AOn4CLAfaETcziKhG4TLVEDP_-EqCdowKw)